Though parochial, an audit of M&A codebases could offer a glimpse of software supply chain risks and vulnerabilities for 2023
By now, anyone remotely involved in software security is like concerned with software supply chain, and for good reason, given the multiple major software supply chain attacks of the past few years.
In today’s digital landscape, software developers can no longer blindly trust that their coding (containing open source materials) is secure. But how do they verify that in today’s highly complex cybersecurity landscape?
One compass is to keep up to date on research conducted around open source security and risk analysis.
In one such yearly report by the Cybersecurity Research Center (CyRC) run by Synopsys, 1,700 audits of commercial codebases (for mergers & acquisition [M&A] purposes) were analyzed with the goal of helping security, legal, risk, and development teams improve their understanding of the open source security and license risk landscape.
Examining such trends and metrics can help developers understand the interconnected software ecosystem they are a part of.
Open source trends and risks in 2023
Adding a five-year retrospective to analyses of 2022 audits, CyRC has discerned the following trends that are expected to continue in 2023:
- All the industries studied made use of a high percentage of open source: Three of the 17 industry sectors audited — Aerospace, Aviation, Automotive, Transportation, Logistics; EduTech; and Internet of Things — contained open source in 100% of their audited codebases. The remaining verticals in the research used open source upwards of 92% of their codebases.
- Despite economic uncertainty, M&A audit numbers remained strong: While 2022’s level of economic ambiguity and a corresponding expectation of global economic challenges in 2023, tech M&A audit numbers remained strong.
- Organizations in the research were not fixing high-risk vulnerabilities: Since 2019, all 17 industries in the yearly research have seen at least a 42% increase in high-risk vulnerabilities, with increases skyrocketing by 557% in the Retail and e-commerce sectors, and by 317% in the computer hardware and semiconductor industry.
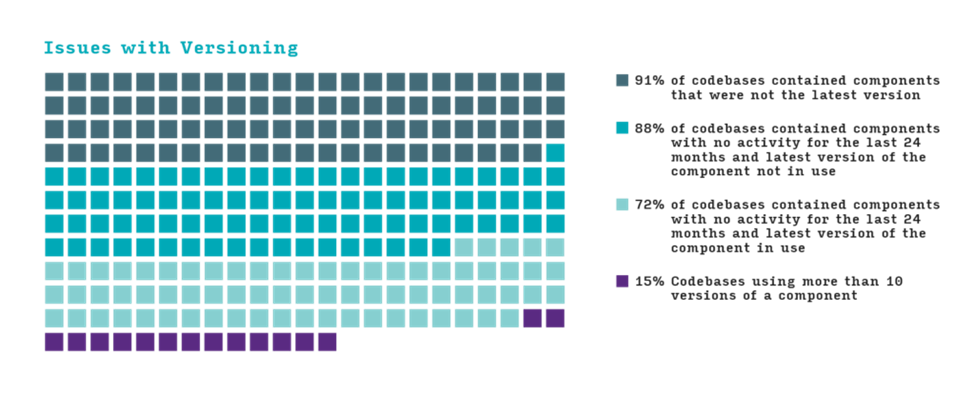
- Patch management is still a challenge: Of the 1,481 of the audited codebases that included security and operational risk assessments, 84% contained at least one vulnerability. Some 48% contained at least one high-risk vulnerability, down 2% from last year’s data. From an operational risk/maintenance perspective, 89% of the 1,703 codebases contained open source that was more than four years out-of-date (a 5% increase from 2022’s report). Also, 91% used components that were not the latest available version.
- License conflicts, Log4j risks endure: 54% of audited codebases for 2022 contained codebases with license conflicts, up 2% from last year. Despite this decrease in high-risk vulnerabilities, more than half the codebases audited contained license conflicts, and nearly half contained high-risk vulnerabilities. Also, 91% contained outdated versions of open source components, where an update or patch was available but not applied, possibly due to DevSecOps teams not being aware that a newer version of an open source component was available. Unless an organization keeps an accurate and up-to-date inventory of the open source used in its code, the component can be forgotten until it becomes vulnerable to a high-risk exploit. That is what occurred with Log4j, and over a year later, it still persists. Vulnerable versions of Log4j were identified in 5% of the total codebases, and in 11% of audited Java codebases.
The report concludes that software supply chain security entails gaining complete visibility into dependencies. In 2023, 96% of commercial code is expected to contain open source, so getting visibility into the components used in your applications should be a baseline requirement for any modern DevSecOps program. A Software Bill of Materials provides this needed insight into business risk and overall security, through which organizations no longer need to trust that they are secure: they can verify it.